
Another Java update? Really?
Sigh.
New updates for Java on all versions of Windows this week (Java 6 Update 41 and Java 7 Update 15), following the emergency Java updates last week, which followed the emergency Java updates the week before that. In fact there have been five Java updates in just over five weeks, 15 in the last 18 months.
Apple released an emergency stop-the-presses get-it-now update for Java on OS X which among other things automatically disables Java in all browsers. Apple is a little sensitive about it, since it had to admit publicly that hackers had exploited a Java flaw and installed Java-related malware on Apple employees’ computers.
Apple’s embarrassing disclosure came on the heels of similar Java-related hacks on Twitter (250,000 user accounts compromised) and Facebook (no user information compromised. Internal data? “No comment.”)
Just uninstall Java. Yank it. This is stupid. Worrying about Java updates is not a productive way for any of us to spend our time.
Hacking efforts directed at big companies have been in the headlines lately. It’s been going on for years but it feels like the pace is picking up. The New York Times published a front-page article acknowledging that its computers had been hacked over a period of four months, including detailed information about its conclusion that the Chinese government was likely behind the attacks.
Twitter, Facebook and Apple made their disclosures. After the New York Times story appeared, the Wall Street Journal and the Washington Post stepped forward with their own reports about being hacked.
Here’s a New York Times article that goes through a few of the many other attacks on large corporations in the last few years, which most hacked companies refuse to acknowledge. “A majority of companies that have at one time or another been the subject of news reports of online attacks refuse to confirm them. The list includes the International Olympic Committee, Exxon Mobil, Baker Hughes, Royal Dutch Shell, BP, ConocoPhillips, Chesapeake Energy, the British energy giant BG Group, the steel maker ArcelorMittal and Coca-Cola.”
Scary stuff.
You probably know that the bad guys try to install malware on your computer when you visit a poisoned web site. Click on a bad link in a spam message, say, and you’re taken to a web page run by the bad guys. It tests your computer looking for a program that it knows how to break – an outdated version of Java, perhaps.
For the last few years, the next thing you would see is a phony security warning informing you that your computer has viruses, with scans showing infected files and bars going across the screen and warning messages about how bad it is. It’s all fictional. They’re not doing a scan, they’re just making up stuff. They’re bad guys. They lie. The goal is to have you put in a credit card number to get the “cleaner.” If it even occurs to you that your computer will come back to normal by paying the money, you really need to think through the concept of “bad guys” more closely.
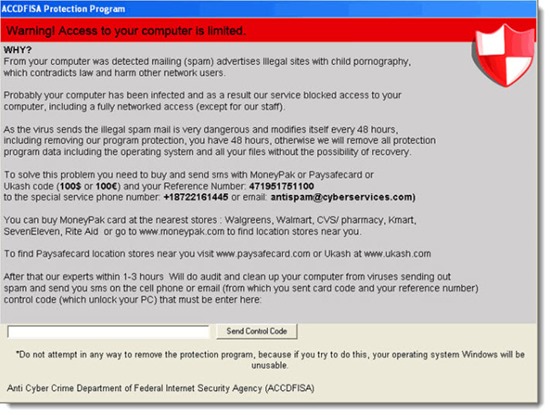
Have you heard about “ransomware”? It’s the latest rage in bad guy circles. It’s a much more naked way to extort money from you when you get malware on your computer. The messages that appear onscreen purport to be from the FBI or another law enforcement agency. Your computer is completely unusable. The message claims that you can regain control of your computer if you pay a hefty ransom. Here’s a sample:
Many of them, like the one above, set out a payment mechanism that bypasses the credit card system to make sure the bad guys get the cash and no trail leads directly to them.
Here’s a New York Times article with more details about ransomware, which is quite a growth industry – millions of dollars a year paid and hundreds of thousands of computers attacked. The malware can be customized for different countries – in the US, you might see a message purporting to be from the FBI; in other countries it might be the local police. Perhaps there will be a webcam stream to make it appear the authorities are watching, or maybe images of child pornography will be displayed with a threat to report you for it if the ransom is not paid.
I have faith in you. You’re not thinking that paying the ransom will restore your computer, right? You’ve got the “bad guy” thing in mind?
Here’s an IT secret for you. Once the bad guys have been on your computer, there is no way to be completely confident that they’re gone without wiping the computer and reinstalling everything from scratch. It’s time consuming and laborious and expensive.
Subscribe to Bruceb Remote Management, or find another way to stay up to date. And be careful out there!

Great article! It used to be that when one found a new virus/MW on their computer and current common tools could not yet fix it, searching on the popup clues one found on the security blogs other folks with your same problem but also were promoting a fix from a never heard before AV-Malware product that you had to buy. Of course, the makers of the solution were the also makers of the AV/MW… Now the bad guys are doing the equivalent of a street corner mugging.