CryptoLocker is a new variety of malware that is genuinely awful. You should be afraid.
Starting now, you should redouble your efforts to live by the Rules For Computer Safety, especially these two:
— Never, never, never open email attachments unless you know with 100% certainty that the attachment is something you expected and want to receive.
— Don’t click on links to web sites that arrive in email messages unless you know exactly where you’re going. Hover over links to make sure they lead where they appear. One of the ways this is spreading is through messages that look real – fake UPS tracking notification emails, for example.
Got that? I’m dead serious. I don’t want anyone I know to have any personal experience with CryptoLocker.
I wrote about “ransomware” earlier this year. It’s a type of malware designed to extort money by holding your files hostage until you pay money to the bad guys. Although it was always difficult to remove, older varieties of ransomware did not actually damage the files. At worst (which was pretty bad), the drive could be removed and the files could be copied off before wiping the drive.
CryptoLocker goes much further.
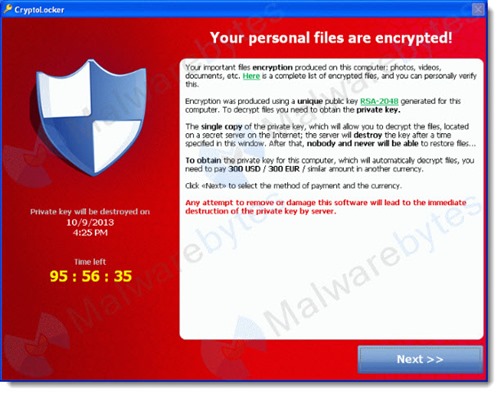
When you run a malicious email attachment with the CryptoLocker code, CryptoLocker silently encrypts your files. After the encryption process is complete, the above window appears demanding payment.
Let’s get straight to the bad news. Once your files have been encrypted, there is no way to get them back. The encryption is quite real and quite strong.
It gets worse for businesses.
CryptoLocker reaches across the network and encrypts all files in mapped drives. If you have shared company files in the M: drive, CryptoLocker will encrypt them if it is run on any computer with permission to access the mapped drive. (Reportedly it will not encrypt files accessed through a UNC path – \\company-server\sharedfolder – but most companies use mapped drives for convenience.)
CryptoLocker encrypts files in attached backup drives. If your backups are stored on an external hard drive, there is a good chance that the backups will also be encrypted. The only backups that are safe are either stored on devices that are not attached to the computer, or stored online. Even some online backups might not be completely safe, because the next backup would copy the encrypted files online. Your backup program would have to allow you to restore previous versions of your files, a feature of most but not all online backup programs.
Worth noting: Dropbox, Skydrive, and other file syncing services are not backups. The encrypted files will be synced to the other computers linked to those folders.
The CryptoLocker ransomware demands a payment, typically $300, using an anonymous online payment service payment method. (It’s not harvesting credit card numbers because that might create a trail to the bad guy bank account.)
A timer begins to run when CryptoLocker has finished encrypting the files and presents the ransom note. If you pay the money before the timer runs out, the malware gets the private security key required to undo the encryption and it decrypts your files, a process that takes several hours. If you don’t pay the money before the timer runs out, your files are gone.
As of a few days ago, paying the ransom was actually working for infected machines. The servers run by the bad guys were responding by pushing the required private key and letting the files be decrypted. At any time, though, those servers may be taken down or the bad guys may decide it’s easier to just take the money and run. Not to mention that paying ransom to bad guys is wrong and repellent in many ways.
Most reports say that antivirus programs are not detecting the CryptoLocker malware, or are not stopping it in time. At some point they’ll catch up but as of today you should assume that you have no protection except your own judgment.
I hate to be an alarmist but this one is ugly and widespread. It’s getting a lot of attention in the security community. There are more details about CryptoLocker from Sophos, from a detailed Reddit thread, and from CMIT Solutions, for example.
ONLINE BACKUPS
Bruceb Cloud Backup, or any other online backup service that keeps previous versions of your files, can help restore your files in the event of a catastrophe. This malware is a good example of why online backups have become popular. If you haven’t set up Bruceb Cloud Backup, give me a call or drop me a note. It takes only minutes to get protected. Get more details here.
Be careful out there!

If you’re looking for Managed IT Services in NYC, Etech7 is the right place for you. I’m a dummy in IT sphere, so all the time I need a good company to solve my IT problems. Finally I’ve found Etech7 and when I need IT Consulting, I’ll definitely call them.
There are so many ways that someones digital information can be compromised, especially if its personal business information (client info, business records, etc.). Having an IT consulting company secure your information is a very smart investment.
Good tip! I’m on my way this morning to work on a computer taken down by Cryptolocker. This is a nasty one! Thanks.