Hackers got an unexpected present this week: a vulnerability in Adobe Flash that can be used to break into PCs, along with detailed instructions about how to use it. Adobe issued a patch within 24 hours, so you’re safe as long as you get the update promptly.
Practical details
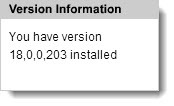
Go to the Adobe Flash version checker in each browser you use regularly. If you have version 18.0.0.203 or later, you are safe. If you have an earlier version, get the latest Flash update from here. Don’t forget to uncheck the boxes for the crapware that Adobe will attempt to bundle with Flash!
If you are a subscriber to Bruceb Remote Management, you’ll get this update next Tuesday but don’t wait – take a minute and go check it out now. This one is worth doing as soon as possible.
The patch is sufficient protection for today, but Flash has become a frequent target. If you’re paranoid and willing to give up Flash content on websites, you can disable it on all websites by following the instructions here: http://www.howtogeek.com/188059/how-to-enable-click-to-play-plugins-in-every-web-browser/ I don’t recommend that; I don’t think Flash is enough of a threat to justify the inconvenience. But we may revisit that if this keeps up.
Background
Hacking Team is a shadowy Italian company that supplies digital spying tools to governments around the world, including the FBI and other US law enforcement agencies. It is the kind of company that makes you despair for the human race. It sells tools to infect computers, steal files, read emails, take photos, and record conversations. Its clients include repressive regimes around the world that use the hacking tools against dissident groups.
Hacking Team was hacked. On Sunday, hackers released a huge trove of files stolen from the Hacking Team servers. The released info is ugly – its products are used for evil ends and its methods are repellent. Here are some details about that if you need a dose of despair.
But it got worse. The released files included vicious hacking tools intended for use by government agencies like the US Drug Enforcement Agency. One of them was a method of attacking Adobe Flash that would allow a computer to be taken over if you did nothing more than go to a poisoned website or clicked on a malicious email attachment. The Flash vulnerability was previously unknown; there are hints in the leaked files that suggest Hacking Team may have been using it for some time.
Hackers immediately weaponized the Flash vulnerability and packaged it into kits that could be used to deliver viruses like Cryptolocker. By Tuesday afternoon, hacking kits targeting the Flash bug were being spotted in the wild, with no patch available. That’s referred to as a “zero-day exploit”, and it’s the scenario that makes security experts break out into a sweat. Malwarebytes called it “one of the fastest documented cases of an immediate weaponization in the wild, possibly thanks to the detailed instructions left by Hacking Team.”
Adobe released its update on Wednesday to patch the vulnerability. Its update mechanisms have improved and you may already have the update. Chrome handles Flash by itself, for example, and Chrome is quite good at installing updates automatically and quickly.
The problem is that Adobe Flash appears to be the punching bag for hackers in 2015. It’s the same process that Java went through in 2012/2013 – repeated attacks, repeated security risks, nonstop updates in futile attempts to stay ahead of the bad guys. The result was that Java stopped being used by developers and was uninstalled from many computers without being missed. The same thing may happen to Flash if this keeps up.
Adobe had to release an emergency Flash update in June to address a vulnerability that was being actively exploited by bad guys. There is a thriving market for exploit kits that hackers can buy as if they’re browsing the shelves at Best Buy, and the Adobe Flash exploits are hot sellers this year. After the June exploit appeared, a Malwarebytes researcher said, “We can expect other exploit kits to follow suit very soon and start delivering this latest vulnerability. Without a doubt, this is the year of Flash zero-days . . .”
There had previously been an emergency update for Flash in February and another one in April for zero-day vulnerabilities, and Adobe has been frantically releasing more routine monthly patches as well.
Install the Flash update and make sure you stay up to date with Windows, Office, and the programs installed on your computer. And remember that there are two proven ways to be safe online:
• Subscribe to Bruceb Remote Management and install the agent on all your computers to get the latest updates for Flash and other utilities installed automatically.
• Follow the Rules For Computer Safety.
Be careful out there!


Hi Bill,
You mentioned that Java was targeted a few years ago, and now it’s not so popular. I’ve heard that HTML 5 can do some of the things that Adobe Flash can do (such as YouTube videos). Could HTML 5 replace Flash completely, or are there some things that only Flash can do?
I’m not a developer but my naive understanding is that new web standards like HTML5 can do amazing things, and make Java and Flash completely unnecessary. Flash has been controversial for quite a while and the shift away from it is well under way. Google moved YouTube off of Flash and onto HTML5 in January, which had a huge impact on the industry. We’re already at the point where security researcher Brian Krebs can write an article about his experience living without Flash for a month, and discovering that he barely missed it. http://krebsonsecurity.com/2015/06/a-month-without-adobe-flash-player/
Flash and Java have been used a lot – entire web empires are built on them. Big changes come slowly, and “standards” turn out to be more slippery than we would guess from the outside. But you’re right, Flash is likely to be a seldom-used option before much longer.