
The bad guys are working overtime. In the last few weeks, two of my clients were shut down for hours or days by viruses that arrived in email attachments. There have been countless near misses with look-alike messages that appear to be from Paypal or from banks, loaded with links to malicious websites. The phony wire transfer requests continue to come in, potentially leading to expensive mistakes. Your employees’ mailboxes are stuffed with messages that could shut down your business with just a few errant clicks.
I’ll tell you a few anecdotes but it’s more important that you refresh your memory of the Rules For Computer Safety – and as always, I encourage you to tape copies of the Rules to your employees’ chairs and distribute them outside local supermarkets and discuss them over drinks after polo matches. Today’s lecture mostly concerns this rule:
Never, never, never open email attachments unless you know with 100% certainty that the attachment is something you expected and want to receive.
Not 99% certainty, that’s not good enough. Also not good enough: any explanation that starts with: “Oh, I thought, maybe . . “ or “It looked like it came from (person known to you), so I figured . . . “ If you get an mail attachment, you must assume it is poisonous and then cautiously convince yourself otherwise. You will want your explanation to be very convincing when you’re repeating it to me while we stare at the ruins of your business.
It’s really that bad out there. It’s one of the reasons that people are fleeing computers and using mobile devices, which are not (yet) easily attacked by viruses. (The other reason is that computers are too damn complicated and it’s amazing that anyone can use a computer without screaming. But that’s another article.)
An attachment that appeared to be a zipped Word document delivered the Cryptowall virus to two clients. It’s the latest variation on Cryptolocker, the worst virus you can imagine, now in circulation for more than two years. I’ve written about Cryptolocker here and here.
When it’s executed, the Cryptowall virus runs silently in the background, encrypting all of your files so they are unreadable. The latest version also encrypts the file names and turns them into long strings of alphabet gibberish to make it more difficult to figure out what files have been lost. When it’s finished, the virus presents a ransom notice (shown above) with instructions about how to send the ransom amount – several hundred to several thousand dollars – by anonymous means to the criminals, who promise to send back a key that will let you decrypt your files. Some people actually get their files back that way but these are criminals, after all, and paying money to criminals and trusting them to play fair kind of misses the point, eh?
The Cryptowall virus is particularly devastating to small businesses because it reaches beyond the computer running the virus and encrypts all files in mapped drives. Almost every small business has an M: drive or a P: drive where everyone stores shared files. It’s the “Company” or “OfficeDocs” or “FirmDocs” folder; the real name might be \\companyserver\firmdocs but most employees call it the M: drive. Cryptowall encrypts those files as well and in a few minutes the business grinds to a halt as all the company files disappear before your eyes.
There’s no choice other than to wipe a computer clean that has been infected by a genuinely bad virus like Cryptowall – reformat the hard drive, reinstall Windows, reinstall all the programs, and set up printers and scanners from scratch. I can remove adware – annoying programs loaded by small-time crappy advertisers – but you can never trust a computer that has had a real virus unless the hard drive is wiped. It’s time-consuming and invariably results in disruption and difficulty getting back to normal.
Restoring files from a backup is no picnic, either. My clients had good backups of the files in the Company/FirmDocs folders but restoring from a backup might mean the loss of work done since the last backup an hour or a day or a week before. In one case, the backup was online, which meant the files were safe but required 18 hours to finish the download from the online backup storage. During that time employees are idle and the business suffers.
Also worth noting: Cryptowall encrypts files in the local copies of Dropbox and OneDrive, both of which then happily sync the encrypted copies online. Theoretically it’s possible to restore previous versions of files stored in Dropbox or OneDrive but only one by one, file by file, which does no good when thousands of files have been encrypted. Include Dropbox and OneDrive in your backups!
Nasty stuff. I’ve also seen a resurgence of email messages that contain links to malicious websites that will attempt to install viruses in the background, or present phony imitations of legitimate sites and attempt to capture your password, or put up phony security warnings imploring you to call a number to clean your computer, or any of a thousand other typical bad guy scams. Take a look at this email message forwarded by a client:
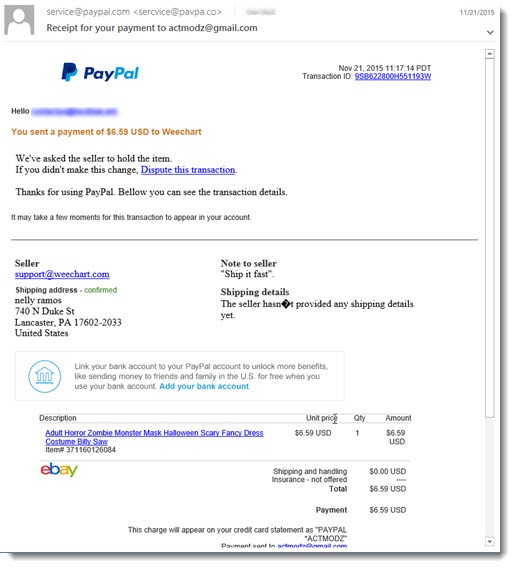
A message from Paypal about a payment you didn’t authorize. Did you notice that the return email address is “sercvice @pavpa.co”? It’s so tempting to click the link that says “Dispute this transaction.” Let’s say you’re careful and you hover over the link before you click to see where it leads – would you notice that it says “www. pvpnal.com” and not “www. paypal.com”? Make a mistake and you’re on your way to a site run by the bad guys (which might also look just like Paypal) and just a click away from a virus disaster.
We’re going to be deluged with email in the next month that appears to be from shopping sites and banks. Some of it will appear to be from companies that you do business with. Our instinct is to completely overlook messages from unfamiliar businesses and just as instinctively to be attracted to a message that appears to be from a familiar name. It’s easy to ignore the message from “Union Bank” and “American Express” and “Bank of America” and yet we’ll pause when a message appears to be from “Wells Fargo” (or wherever you bank) because, who knows, maybe it’s real. Look hard before you click!
Paranoia is your best defense. Your antivirus program may not defend you. (Security programs fought with the Cryptowall virus in both cases for my clients but did not stop it until most of the damage was done.) Review the Rules for Computer Safety, and please, please, be careful out there.


Hi Bruce,
I really like Soonr, I’ve been using them for a couple of years now and the product and support have been outstanding.
There are a few caveats though:
a) The autotask takeover worries me, they took over in July and all the useful Soonr website pages have disappeared, you’d think they would have sorted it by now.
b) Soonr doesn’t do lan-sync which has been promised for next year, but with the takeover, who knows.
I met Stephen Boye, one of the Soonr founders here in Sydney just after the autotask acquisition, and he’s a top bloke. So I remain hopeful…
Regarding Dropbox I’m pretty sure they told me I could do it myself, I’ll have to find the email.
But this page describes “Account Rollback” here:
https://www.dropbox.com/help/400
Hi Bruce,
I love your site, and your articles have helped me a great deal in my own IT business.
Just a few points regarding your article above:
1) Dropbox does allow you to restore all your files to a point in time, I checked with them.
They are one of only a few that do, again I checked and I was shocked that most don’t.
Those that do:
Residential
Dropbox
Mozy Home (Backup only, not sync)
Commercial
Dropbox for Business
Soonr (my favourite)
Securisync
Note that you have to ask for this to be done with everyone except Dropbox, which you can do yourself.
The ones that don’t:
GDrive, OneDrive, Syncplicity, iCloud, Sugarsync etc, there’s about 10 I asked….
2) Recovery from Cryptowall
Here’s what I do for Corporates:
a) Soonr for File Syncing, Macrium Reflect for backups, Quarterly offsite backups at Client’s house.
b) The Macrium Backups are written to the Synology, to a password protected folder. However only Macrium knows this password.
None of these folders can be mapped, so none of the the PCs can infect them, for the moment anyway! 🙁
c) All Company files are also backed up to Amazon S3 using a combination of Cloudberry and Synology. There are 5 revisions kept for all files.
d) All files and Macrium Backups are copied quarterly to external usb drives which are then stored in the Client’s home in a safe. There are 6 months worth stored.
3) Recovery
If a Cryptolocker variant did hit us and spread to all PCs, here’s what we would do:
a) Restore from yesterday’s Macrium backups, this would only take about 15 mins due to Rapid Delta Restore. I’ve tested this and 15 mins is real using a computer with a ssd drive.
b) If the Soonr or Dropbox files have been encrypted, then restore to the point just before. This is where the most delay could occur.
However we could restore individually to recover files that people were working on.
c) Soonr is smart enough (so is Dropbox) to recognise that the PC’s files have changed and downloads the files that were changed since yesterday. These files would be the recovered unencrypted files from b) above.
d) If somehow the backups on the password protected folders were encrypted, we would recover from the offsite copies.
These would be an average of 6 weeks out of date, but again Soonr is smart enough to realise that and download the last six weeks of files.
e) If all that failed, we would recover from Amazon S3 plus some spare usb drives I have lying around 🙂
I haven’t tested e), I hope I never have to 🙂
So there you have it, a bit paranoid I know! But quite easy to set up.
Best wishes, Martin
Thanks for taking the time to write that down! It’s a lot of good information. Dropbox will allow you to restore to a point in time? I’m going to scurry off and find out more about that – I didn’t know that and it’s very cool – and maybe very important to people choosing services in this paranoid age. I’ll go look at Soonr, too, that’s a new name to me.
I’ve got a similar setup in many clients’ offices using a combination of ShadowProtect (magical backup software), an onsite Synology, offsite storage of backups at my office, and Cloudberry as an extra bit of insurance for the data. http://www.bruceb.com/backuppro I hope neither of us have to use any of it!
Thanks!
I chuckled when I pulled up the Soonr site. I didn’t realize it was part of the Autotask family. I was in a long demo session with them this morning, looking at their endpoint management, but we didn’t talk about Soonr. I’ll check it out!