The bad guys aren’t kidding around. They’re after you. Some day soon you will be walking down the street and a 400 pound hacker will galumph out and make a scary face and shout, “Give me all the passwords in your wallet!” and stomp off cackling and steal all your money from his couch. Or maybe it will be Russians. I always get them confused.
I had two clients in one morning with hacked email accounts. They were both the scary full-fledged bad-guys-have-the-password kind of hacks. In each case, the bad guys were running the wire transfer scam (more about that below). Fortunately neither of the clients lost money. But we know the bad guys were rummaging around in the mailboxes and there’s no way to know what other information they got that might be harmful later.
We don’t know how the bad guys got the passwords. Typically your password is hacked in one of three ways: (1) You had a different account that was already compromised; (2) You downloaded a malicious program on your computer without knowing it; or (3) You accidentally gave your password to someone without knowing it.
The wire transfer scam, though, is a specific, focused attack on you, by bad guys that study your website and LinkedIn page and social media postings. The bad guys have more powerful computers and better algorithms to try to crack your password by brute force. They’re going to start that attack by feeding in your business name, your spouse’s name, your kids’ names, your pet’s name, your phone number, your address, your anniversary, your kids’ birthdays, and any other bits of information they can glean. The algorithms will test every combination and variation of those terms to try to unlock your account.
Ever posted a cute picture of your dog named Booger on Facebook? Is your password “Booger123”? Approximate time for the bad guys to crack your password: 8 seconds, including the time spent on booger jokes. (That’s an inconsiderate name, by the way – the other dogs are making fun of him and hurting his self esteem.)
If any of your passwords is your pet’s name or your spouse’s name or a child’s name, change your password.
If any of your passwords is a dictionary word that you’ve cleverly disguised by starting it with an upper case letter and ending it with an exclamation point, change your password.
If you’ve used the same password in more than one place, change your passwords.
No more excuses.
Need help with passwords? This article has a short list of suggestions, including a foolproof tip for creating unique passwords that you can remember. Seriously, it’s one of my best tips. Put it to good use.
The wire transfer scam
Two years ago I wrote this article about the wire transfer scam. It’s still going strong.
The wire transfer scam starts with a short note to the person most likely to be able to approve a wire transfer for you or your company. It might appear to be an email from you to your investment advisor, or it might appear to be from a manager or executive and sent to the bookkeeper. The bad guys have done research to make the scam more believable. They might wait until the executive is on vacation – which they learn from Facebook. They might register a domain with a confusingly similar name to intercept replies.
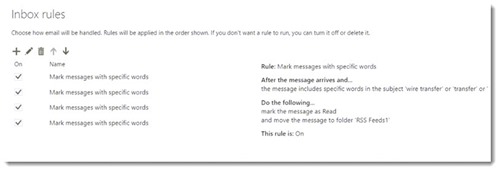
For each of my clients, there were details in the messages to make them believable. One of them had the executive’s email signature and identifying information about the company bank account – which the bad guys had learned from searching through the mailbox. Since the bad guys had hacked into the mailboxes, the messages requesting wire transfers came from the actual executive mailboxes. The recipients had no obvious warning that the messages were phony.
In each case, the bad guys added a rule to Outlook to divert replies into an obscure Outlook folder, then deleted the messages, then “permanently” deleted them from the Deleted Items folder. We were able to find them in the Office 365 Super-Secret Deleted Items repository behind the scenes.
The FBI issued a warning in May that wire transfer scams sharply increased in the last half of 2016. From Reuters: “Attempts at cyber wire fraud globally, via emails purporting to be from trusted business associates, surged in the last seven months of 2016, the U.S. Federal Bureau of Investigation said in a warning to businesses. . . . The number of business-email compromise cases, in which cyber criminals request wire transfers in emails that look like they are from senior corporate executives or business suppliers who regularly request payments, almost doubled from May to December of last year.”
Here’s an example of how insidious this scheme is. Hackers have been targeting the real estate industry, stealing details of pending home sales. When the closing date approaches, the hacker sends an email to the buyers instructing them to wire the purchase money to a different account. Every detail in the email is perfect. If the buyer follows the instructions, poof! The money is gone, and so is the dream of buying the house. Here’s an article with more details about the real estate wire transfer scam.
Earlier this year the IRS issued a warning about W-2 phishing, a variation on the wire transfer scam. The bad guys do the same research and hack into an executive’s email account, if possible, then send a request for employee W-2 information. If they can get W-2 information, they can file fraudulent tax returns and collect tax refunds, or engage in other forms of identity theft.
Don’t let the bad guys into your mailbox! Your first line of defense is a strong collection of passwords. If your password is a string of two or three things that can be guessed (“Hint: street name + anniversary”), that’s not much better than using 123456 as your password. Step up your efforts to be secure!