
I want to talk to you about two-factor authentication and why you should use Authy to generate codes on your phone.
Oh, come on! Don’t give me that look. I know you don’t want to think about this stuff. It’s roughly like having an insurance salesperson look you in the eye and ask you if you’ve thought about what will happen to your family after you’re gone. But stick with me for a few paragraphs, at least until I get to the geeky details at the end.
TL;DR
Two-factor authentication (2FA) adds an extra step to the process of logging into an account – LastPass or your Google account, for example. The extra thing might be a code sent as a text message to your phone or a number generated by an app on your phone.
The combination of 2FA and a password is far more secure than having just a password, even if the password is complex. This is the important part. From a security perspective, it’s like night and day.
Using an app on your phone is more secure and more convenient than waiting for a code to arrive as a text message.
Authy is the best way to set up 2FA. It’s a free app for iOS and Android. It’s similar to Google Authenticator (and fully compatible with all sites that can be set up with Google Authenticator), but it has some significant advantages: Authy can be secured on the phone; it can be securely backed up and transferred seamlessly to a new phone; and it can be used on a computer.
The basics of two-factor authentication
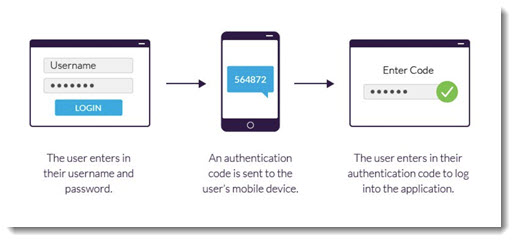
When two-factor authentication is turned on for one of your accounts – Google, LastPass, your bank – you have to enter your password, PLUS you have to supply a code sent by SMS or a number generated by an app.
When you set up two-factor authentication, your account is still secure even if the password is hacked. If an account is secured by 2FA, then the bad guys can’t get into the account even if they get the password. They’ll be asked for the other thing – the text message code or the number from the app on your phone – and they won’t have any way to supply it.
Some services (including LastPass and Google) allow you to check a box for the service to trust the device that you’re using at that moment – perhaps permanently, perhaps for two weeks or a month. When you use that service, you won’t be asked for the code because you trust your own phone or your laptop. The effect is that the inconvenience is minimized day to day, but you still get increased protection, because the extra step will still be required if anyone tries to sign in to your account from another device.
Use an authenticator app instead of text messages

Text messages are the most common way to handle two-factor authentication. Your account is set up so it cannot be opened until a six-digit code is typed in. The code is sent by text message to the phone number that you have on file.
For security, this is far, far better than nothing. Seriously, if there is any way to turn on 2FA for a sensitive account, you should use it, even if an SMS code is the only option.
Authenticator apps are easier to use and more secure than text messages, because bad guys can hijack SMS codes. From Wired:
“Unfortunately, it isn’t that hard for thieves to impersonate you to your mobile phone carrier and hijack your mobile phone number—either with a phone call to customer support or walking into a phone store,” says Lorrie Cranor, a computer scientist at Carnegie Mellon University and former FTC technologist who had her own SIM stolen in 2016. Authenticator apps are not vulnerable to this problem, and thus are a more secure way to do two-factor verification.
An authenticator app generates codes every 30 seconds. There are authenticator apps from Google, LastPass, Microsoft, and others.
Not all services support all authenticator apps. Google Authenticator is the most widely supported; almost every site that supports 2FA works with Google Authenticator. Down below, I’ll tell you other reasons I recommend Authy, but an important one is that it is fully compatible with Google Authenticator.
After you install the authenticator app on your phone, setting it up for one of your accounts is usually easy. Log into your LastPass Vault, for example. In Settings / Account Settings / Multifactor Options, choose two-factor authentication with Google Authenticator. In the next window, you’ll see a barcode. On your phone, you’ll open Google Authenticator or Authy and hold it up so the camera can see the barcode. That’s all there is to it. In a second or two, the authenticator app begins generating codes for LastPass.
Why Authy is the best authenticator app

Tech articles frequently tout apps that have the most “features,” without considering whether the extra functions actually matter to real people.
Authy has unique extra features that are important for everyone. I wouldn’t recommend it otherwise.
Let’s compare Google Authenticator and Authy.
Ease of use
Google Authenticator is swell. It’s simple and easy to use and free. It is the most widely supported authenticator app.
Authy is also swell, also simple, also easy to use, also free. It has one significant advantage over, say, the authenticator apps from Microsoft and LastPass: Authy can be used at any site that supports Google Authenticator.
It’s a tie so far.
Startup security
If your phone is logged in, Google Authenticator starts right up when you click the icon. Authy can be set up so that a PIN or fingerprint is required before the Authy app starts up. That’s a pretty small risk, but it counts. Advantage Authy.
Lost or stolen phone
Remember, each account is set up separately to work with an authenticator app. If you set up 2FA for your Google account, for LastPass, for your bank, and for one or two other accounts, and then your phone is lost or stolen – well, it’s a pain to get access to those accounts. The whole idea of 2FA is to make it difficult or impossible to access those accounts from a different device. If it were easy – if you could reset 2FA with nothing more than typing in your mother’s maiden name – well, then, 2FA wouldn’t be much extra security, would it?
Security digression: The weakest link for security today is frequently the process of resetting a password, rather than the password itself. That’s why the bad guys try so hard to get the password for your mail account. Once they’re in your mailbox, they can reset all the other passwords that require only a click on a link in an email message.
Google Authenticator doesn’t help you with resetting 2FA for a lost or stolen phone. For each account, you’ll have to go through phone calls or a lengthy sequence online to establish your identity and authorize a new phone.
Authy can back up your 2FA information in a secure way online, so it can be restored on a new phone and have you up and running immediately.
This is Authy’s most important advantage. Authy uses the same technique that LastPass uses to keep your information secure: your 2FA account information is encrypted on the phone and secured with a backups password. Authy gets only an encrypted blob. There would be zero risk even if bad guys hacked Authy’s servers and stole everything. When you get a new phone and install Authy, your new phone downloads the blob and decrypts it with the backups password. You’re connected to your 2FA accounts automatically and instantly. Here is Authy’s explanation of the security that protects your online backups.
Do not forget the Authy backups password
It’s just like LastPass. If you forget the Authy backups password, you’re locked out. You will take out your anger on your pets and nearby loved ones.
The best place to record the Authy backups password is in LastPass.
Geeky details about setting up Authy for maximum security
- In the Authy settings for App Protection, set it to require a PIN or fingerprint to unlock the app.
- In the Authy settings for Accounts, turn on Backups and assign a backups password. Write it down or record it in LastPass.
- In the Authy settings for Devices, turn on Allow multi-device. On your desktop PC or laptop, log into the Authy website and add your computer as an additional authorized device. The computer copy of Authy will have a separate master password, different from the backups password. Here is Authy’s explanation of its different passwords. Write it down or record it in LastPass.
- Once that’s done, go back to the app and turn off multi-device. Here is Authy’s explanation of why that is the final step to prevent anyone from hacking into your account and adding a rogue device.

I just recently set up Authy to be my 2fa and I use a finger print or pin as a lock on opening the app. I set the master password which is also the backup recovery password as the same master password I use to unlock my LastPass account because it’s very difficult to crack. I have also set up LastPass to be secured using Authy so it requires a code to access it. I now am wondering if there is any sort of vulnerability in this scenario. I’m thinking if somehow Authy got hacked and my sign on (backup) password gets hacked then they would be able to access my LastPass vault. Perhaps everything is encrypted and all is ok but was wondering your thoughts on that and if I should go back and change my Authy password. Thanks
PS I loved your explanation about this whole 2fa stuff. I wish I had found it before I decided to go with Authy because you explained it perfectly.
Thanks for your help
Once you focus on security, there’s no limit to how paranoid you can be. And it’s all justified! Big companies, small companies, individuals – there are attacks at every level.
So there’s no “right” answer to your question. But you already know the answer you should choose. The general rule is, never use the same password twice. If it’s hacked in one place, the bad guys may test other places to see if you used the same password. It’s hard to imagine the sequence of events that would put you at risk – but it’s not impossible to imagine. And that means you shouldn’t re-use the LastPass master password. It’s the key to your kingdom. It deserves the highest level of protection.
Thanks for your fast response. The more I am thinking about the more I agree with you. It’s a infinitesimal chance of a problem but like you say why risk it.
Yes they started doing this.
I would agree that using an app based authenticator is more secure than having the OTP code sent via SMS, but I would argue that a hardware token is more secure as they are fully self contained and impervious to viruses and spyware. A lot can also be said for FIDO keys, but most Fido keys require a connection to a USB port (and this opens up different security issues).
You’re probably right for the small number of people who need the highest level of security. But I’ve watched my wife wrestle with her hardware token over the years, trying to figure out how to re-authenticate it and periodically exchange it), and it just will never be a good solution for most people. Journalists, human rights activists, people working in countries with difficult governments, and deeply private people – different concerns, different techniques than what I suggest.
Hayley Bentley hb2031369@gmail.com X box
If you use LastPass to generate and store a strong and hard to memorize password for Authy, and you also have LastPass set up with 2FA, what is a best practice to prevent a scenario where you loose access to both Authy and LastPass? Said diffently, I can’t log into LastPass without 2FA (Authy), but I can’t log into Authy without the password which is stored in LastPass. Would like to understand the best practices, ideally without the need to reach for recovery codes.
I don’t have a definitive answer. You’d have to look for advice from people with more experience and authority. Authy has a special role, so I’ve recorded its password in a separate place, in addition to LastPass. But more important, on a mobile device, I’ve authorized Authy to log in with biometric info – fingerprint – instead of typing in the password. You’re right to think it through – don’t get locked out without a back door of some kind, even if it’s a piece of paper in the drawer with the Authy password.
Do you have any experience with physical security keys? I’ve been considering purchasing a YubiKey 5Ci and now wonder how this device compares with Authy from security and convenience viewpoints. TIA!
I’ve got two Yubikeys – one in my possession, the second in a safe place in case the first one is lost. They’re complementary with Authy.
* Some sites don’t take Yubikey but can be set up with Authy/Google Authenticator.
* Think about what happens if you set up a Yubikey and then lose it. There’s always a second way to recover access to the account, and that’s the weak link from a security standpoint. So the backup method is set up with Authy. I have LastPass and my Google account set up that way.
Once you authenticate with the Yubikey and trust devices that are likely to be safe, it’s reasonably convenient. I have to pull out the key once every week or two for something or other – not bad!
Interesting. But what about LastPass? It backs up my 2FA just fine. (the Lastpass Authentication app, totally separate from the normal LastPass App) Is Authy better than it in some other way?
I haven’t used the LastPass Authenticator but it appears to be just great. It has many of the same features as Authy for backups. If it meets your needs, absolutely, use it. If you’re choosing one from scratch, Authy/Google Authenticator is accepted at many more sites. It’s frustrating if you want to use 2FA but can’t use the authenticator you’ve chosen because a service doesn’t support it.