Two weeks ago my son clicked OK on a message about some security problem. He called out and asked me about it after he clicked. By the time I walked in and unplugged the network cable, there were seven malware startup programs and services installed and over 700 files in C:, C:Windows, C:WindowsSystem32, and a few other places. He got lucky; I know some tricks and cleaned them out successfully.
Last week a Windows XP computer was discovered by a client in a closet where it had been sitting for three years. He brought it to the office and plugged it into an Internet connection. Within 15 minutes it was dead, killed by an accumulation of viruses and spyware. It blue-screened in an ugly way that was clearly going to mean reformatting the drive. He bought a new computer.
The bad guys are still out there.
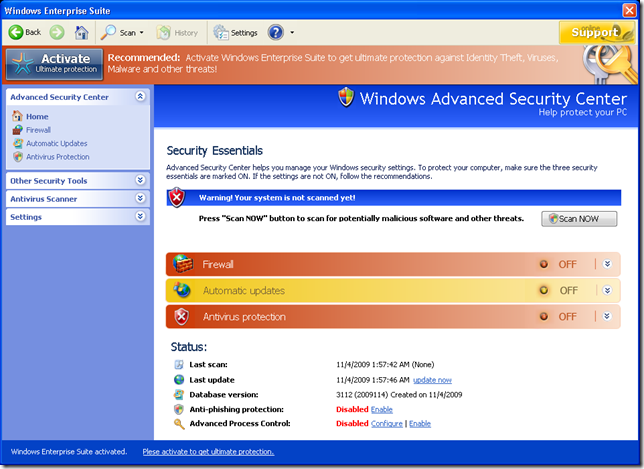
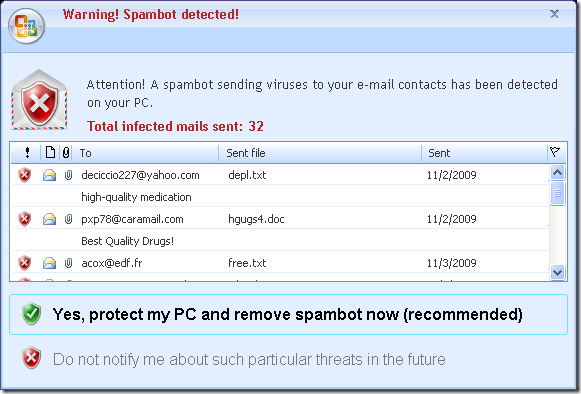
The most prevalent malware comes from rigged web sites that bring up realistic security warnings, similar to the one above. (Screen shots come from a recent post by the Microsoft Malware Protection Center.) The spelling and grammar are correct and the artwork mimics real Microsoft screens. Here’s a phony screen that uses the Microsoft Office logo to lend authenticity:
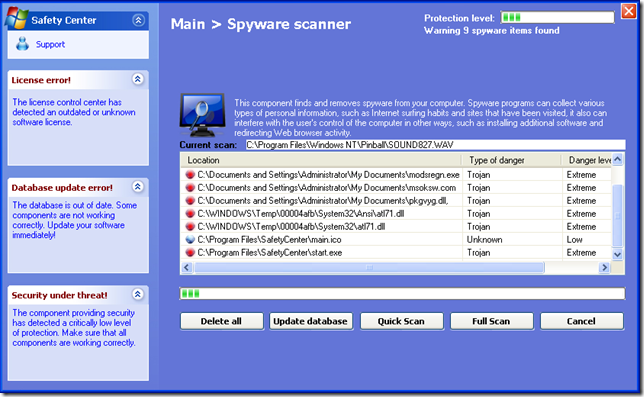
The screens are phony. The “reports” are fictitious. If it pretends to be doing a scan, it is not; it is showing you artwork and fake information.
The best of this type of malware is only trying to get money. Every single thing you click on will take you to a payment screen. If you put in your credit card number and you’re lucky, you’ll only get charged $49 for nothing whatsoever. If you’re unlucky, you’ll suffer the consequences of giving your credit card information to criminals.
The worst of this type of malware will corrupt files used to run Windows, making it impossible to use your computer. Perhaps the malware runs instead of Windows Explorer when you restart the computer, or perhaps it prevents you from going to any web site, or even brings down your computer completely.
The bad guys primarily do it for money now, although there are a fair number of malicious hackers too. Here’s an analysis of one of them from last year.
It’s up to you! Here are three important excerpts from my Rules for Safe Computing.
Antivirus software & UAC will not always protect you against malware if you click OK at the wrong time. The bad guys are liars. They will say anything to get past your defenses, without conscience or remorse. Use your common sense. Read and think before you click OK.
Don’t click on links to web sites unless you know exactly where you’re going.
- Follow links with carefree abandon to and from legitimate sites, but don’t click on links that arrive in spam e-mail, instant messages, web forums, or IRC chats, or that start from an untrustworthy web site.
- Don’t click on links in email messages unless you deeply trust the judgment of the person who sent the message.
- Don’t click on links in forwarded messages.
- Shortened links are becoming popular in Twitter, Facebook, blogs, and social networking sites. You can’t tell where they lead by looking at them. Don’t follow them unless you trust the person who created the link.
If a web site brings something up on your screen that might be malware, do not click on anything. If you click “NO” or “CANCEL,” there is a good chance that they lied and you actually gave permission to install the malware.
- If there is any chance that a dodgy web site is on the verge of installing a bad thing on your computer, start Task Manager and kill Internet Explorer from the list of applications there.
- If that’s not sufficient to close the possible malware window, see if you can identify it in the longer list of “Processes” in Task Manager.
- If neither of those work and you still have a window onscreen that might be dangerous, turn your computer off with the power button.
The screen shot below is another bit of malware posing as security software. There are hundreds of variations of these screens out there.
Be careful out there!

Trackbacks/Pingbacks