Cryptolocker is arguably the worst virus we have ever faced. It first appeared last fall and caused havoc, then left the news for a few months.
It’s back. I’ve had two clients lose computers to Cryptolocker or a variation on it in the last month, and there are reports that it is spreading worldwide.
I’ll give you a basic description of Cryptolocker, some info about its resurgence, and some ideas about how to protect yourself. The best protection is a strong online backup of your files; Bruceb Backup Pro is specifically designed to allow businesses to recover from a malware disaster.
BACKGROUND
Cryptolocker and its variants are “ransomware,” a type of malware that holds your files hostage until you pay money to the bad guys. (And if you believe the bad guys will unlock your files after you pay the money, you’ve missed a fundamental part of the concept of “bad guys.”)
Here’s why it’s so bad.
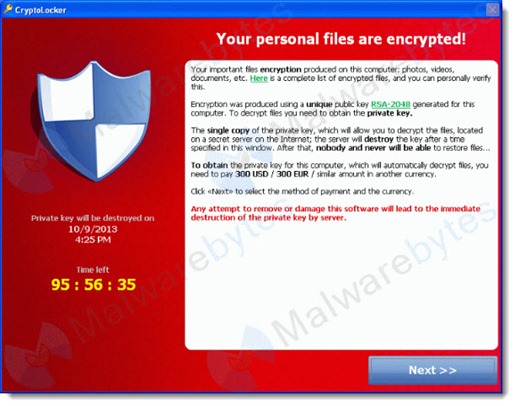
When you run a malicious email attachment or are led to a poisoned website with the CryptoLocker code, CryptoLocker silently encrypts your files. After the encryption process is complete, the above window appears demanding payment.
Once your files have been encrypted, there is no way to get them back. The encryption is quite real and quite strong. That’s all of your Word documents and Excel spreadsheets and PDFs and pictures and Outlook archives and much more – gone. Poof!
It gets worse for businesses.
CryptoLocker reaches across the network and encrypts all files in mapped drives. If you have shared company files in the M: drive, CryptoLocker will encrypt them if it is run on any computer with permission to access the mapped drive.
CryptoLocker encrypts files in attached backup drives. If your backups are stored on an external hard drive, there is a good chance that the backups will also be encrypted. The only backups that are safe are either stored on devices that are not attached to the computer, or stored online. Even some online backups might not be completely safe, because the next backup would copy the encrypted files online. Your backup program would have to allow you to restore previous versions of your files, a feature of most but not all online backup programs.
Worth noting: Dropbox, OneDrive, and other file syncing services are not backups. The encrypted files will be synced to the other computers linked to those folders. You might be able to use their built-in features to restore a previous unencrypted version of the files but only one-by-one, file by file – essentially useless if you have a lot of files.
THE RETURN OF CRYPTOLOCKER
I wiped out a client’s hard drive last month and reinstalled Windows and all programs from scratch after Cryptolocker destroyed all the files. It was an expensive disruption. It wasn’t the only one that I have personally dealt with recently.
The first report I noticed this year came in an article in April about mass Cryptolocker spam sent to UK computer users. In May, a Washington news station covered the spread of Cryptolocker.
LegalPro, the vendor of widely-used law office programs, sent out an urgent warning to all of its customers about Cryptolocker last month after finding out from multiple law office customers that Cryptolocker had encrypted the program databases and files.
Although I didn’t hear personally about any Cryptolocker attacks between January and April, Cryptolocker attacks and copycats have actually been increasing steadily worldwide. Last week law enforcement took down a number of ransomware servers but UK’s National Crime Agency warned that their action might provide a respite for no more than two weeks, and perhaps less, until the bad guys have set their networks back up again. From an article today about the takedown:
“Jeremy Demar, director of threat research for Atlanta-based Damballa Inc., and who participated in the FBI sinkholing operation, said CryptoLocker — along with other ransomware variants — was such a runaway success that it would be incomprehensible for attackers to move away from ransomware. ‘Crime is a business, so attackers are going to go wherever the highest return on investment [ROI] is,’ Demar said. ‘Right now, ransomware and click fraud seem to be the highest ROI they have, so they’ll continue to pick up in these areas.’”
HOW TO BE PROTECTED AGAINST CRYPTOLOCKER
Starting now, you should redouble your efforts to live by the Rules For Computer Safety, especially these two:
– Never, never, never open email attachments unless you know with 100% certainty that the attachment is something you expected and want to receive.
– Don’t click on links to web sites that arrive in email messages unless you know exactly where you’re going. Hover over links to make sure they lead where they appear. One of the ways this is spreading is through messages that look real – fake UPS tracking notification emails, for example.
An online backup can be the most effective way to recover your files if Cryptolocker takes over your computer. The backup program has to be able to restore a previous version of your files, in case the backup program runs and backs up the encrypted version of your files.
Bruceb Cloud Backup retains multiple versions of your files and allows a point-in-time restore in a single operation.
For businesses, Bruceb Backup Pro combines ShadowProtect and Bruceb Cloud Backup to provide multiple levels of protection, with onsite, offsite, and cloud versions of the files available in a crisis.
It is more crucial than ever to keep your computers up to date. Bruceb Remote Management installs security patches and updates on home and business PCs. It’s an inexpensive way to improve the security of your computer.
Contact me if you want to take advantage of any of these services, or if I can be of any assistance. Be careful out there!


Trackbacks/Pingbacks