Virus emails from the bad guys have been steadily getting more sophisticated and harder to spot, but careful proofreaders have almost always been able to find errors in spelling and grammar that give them away. “Your mailbox has exceeded the storage limit may can not to receive email until you Upgrade. plese click the button to Upgrade.”
You can’t count on that any more. In fact, you’d better bring your best proofreading skills – and possibly a magnifying glass – to scrutinize your email messages before you click on a link. The bad guys are sending messages that appear to be 100% legitimate. They’re starting to use tricks that make it hard to tell that links lead to evil places, even if you hover over the links and study where they really lead.
This is a scary story about how hard the bad guys are working to fool you. If you’re not hovering over links in email and on web pages before you click, please go back and read my article and make it a habit today.
This is a message that a client got from Microsoft last week.
It looks exactly like a real message from Microsoft. If Microsoft sent a password expiry message, that’s what it would look like. I can’t confirm it but maybe it started as a real Microsoft message. In any case, no spelling mistakes, no grammar issues, absolutely rock solid formatting: no giveaways. (The client’s email address is not blurred in the original message, of course.)
Fortunately my client has been brainwashed by my barrage of sky-is-falling security warnings, so he hovered over the link in the message before he clicked. When he saw that it was a legitimate link to the Microsoft Office 365 portal, he clicked, got to the Microsoft password reset page, entered his current password, then his choice of a new password.
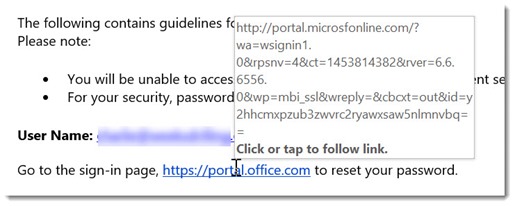
This is what the link looks like when you hover over it. Admit it, you’d click too, right?
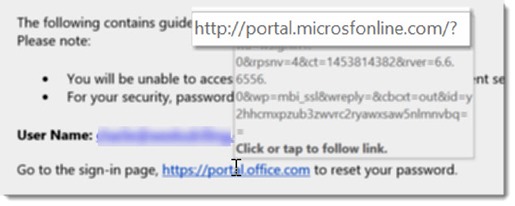
A day later he tried to log into webmail and his new password didn’t work – but the old one did. Strange, he thought. And only on further study did he figure out the scam. Do you see it? Here’s a close-up of the first line of the link in the popup when you hover over the link in the message.
It leads to “microsfonline.com,” not “micros _o_ f _t_ online.com.” The bad guys registered a phony domain name that’s designed to be misread.
Obviously the “password reset” page was phony. The bad guys got the current password for the Office 365 mailbox, which gave them full control of his mailbox for 24 hours before he changed the password and regained control. He’s trying now to find out how much damage was done. Remember, controlling a mailbox means the bad guys can gain access to all online services connected to that email address. Almost all services – banks, shopping, etc. – will let you reset an account password by responding to an email message. If the bad guys control the mailbox, they can reset all the other passwords.
There are two things that are scary about that story.
One is the sophistication that the bad guys showed in copying or crafting a message with no giveaways whatsoever in the look and feel of the presentation and no errors in spelling or grammar. You have to depend on your paranoia more than ever. If you get a message that you’re not expecting or that causes you to have even a twinge of doubt, stop and move very carefully while you check it out.
The other is the deliberately confusing domain name. The bad guys can register domain names freely. Perhaps they’re only in existence for a few days – long enough to run one scam before switching to a different one. Long time readers will recall that bad guys targeting specific companies for the wire transfer scam will register a name that is similar to a company domain with just a single change that might be easily misread. If you get a message with a link to wellsfargonline.com or wellsfargoonlline.com (made up examples, I hasten to add), will you notice the typos? The bad guys are counting on you to overlook them.
Hover over links before you click on them. And more than ever, be careful out there!